Why Cloud Infrastructure Matters in Guard Tour Accountability
Security operations rarely fail at the moment of action. They fail later — when proof is required.

* Card payments are processed by Stripe; Trinity Guard® does not store sensitive card data.
Security operations rarely fail when you need them
Security operations rarely fail at the moment of action. They fail later — when proof is required.
Paper logs, spreadsheets, screenshots, and disconnected systems may appear sufficient during daily operations, but they collapse when accountability is tested. In modern security environments, the ability to prove what actually happened is no longer optional.

Guard tour verification is not a feature — it is an evidence system
Guard tour platforms are often described as software tools. In reality, they function as evidence systems.
Every patrol record, checkpoint verification, vehicle entry or exit, incident photo, and timestamp may eventually be reviewed by:
- clients,
- auditors,
- insurers,
- legal teams,
- or regulatory bodies.
If the underlying system cannot guarantee data integrity, traceability, and availability, the platform fails — regardless of how polished the interface looks.
True accountability requires:
- consistent time synchronization,
- tamper-resistant records,
- controlled access,
- reliable storage,
- predictable system availability.
These guarantees do not come from user interfaces. They come from infrastructure.
To understand how these guard tour principles work on users’ devices, see our detailed overview of how the guard tour app works on Android and iOS .
Why cloud architecture determines trust
Cloud infrastructure is often discussed in terms of scalability or cost efficiency. In security operations, its real value is different.
Cloud architecture removes doubt.
When patrol data is stored locally, manually exported, or fragmented across systems, critical questions arise:
- Who created this record?
- When was it generated?
- Was it altered?
- Can the data be independently verified?
A properly designed cloud-based system answers these questions by design, not by explanation.
This is why modern guard tour and patrol verification platforms must rely on infrastructure that supports:
- centralized and immutable data handling,
- role-based access separation,
- audit-ready logging,
- high availability without local dependencies.
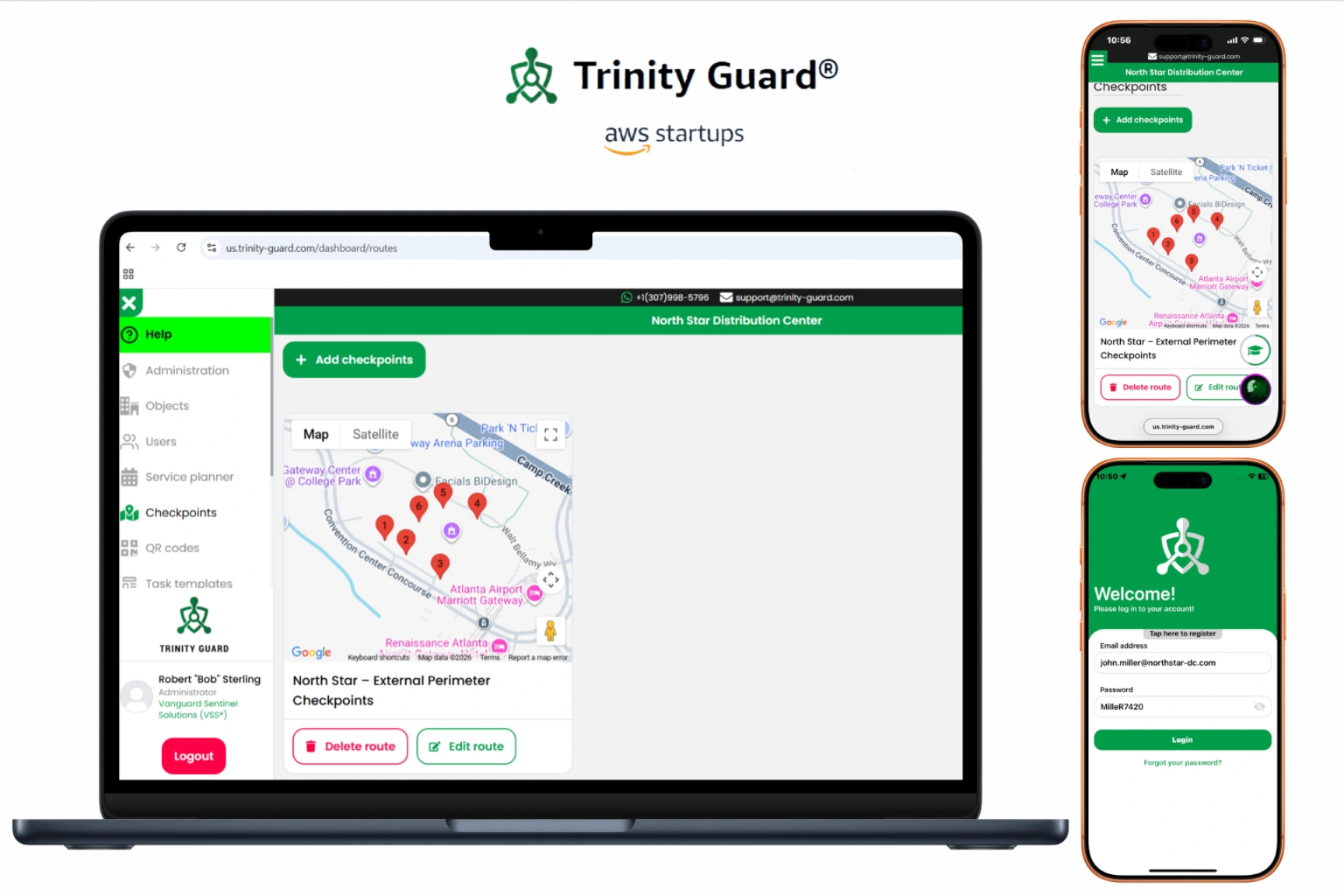
How Trinity Guard® approaches accountability
Trinity Guard® was designed from the outset as a verification-first platform, not a reporting tool.
Patrol execution, checkpoint verification, vehicle entry and exit logging, and incident reporting are treated as operational evidence, not discretionary user input. The system is built to preserve original records, maintain consistent timestamps, and support real-time supervision without altering source data.
This approach requires infrastructure capable of supporting:
- reliable event logging,
- secure data retention,
- multi-site operations,
- and long-term operational consistency.
Why AWS matters in security verification systems

Infrastructure choices signal intent.
Platforms built on enterprise-grade cloud infrastructure demonstrate that:
- data integrity is a priority,
- availability is non-negotiable,
- and security operations are treated as critical systems.
For this reason, Trinity Guard® operates on AWS cloud infrastructure.
AWS provides globally trusted availability, mature security primitives, and compliance-ready building blocks that support long-term operational reliability. These are not marketing advantages — they are risk-reduction mechanisms for organizations that depend on defensible security operations.
Trinity Guard® operates on AWS cloud infrastructure and is officially listed in the AWS Startups Showcase, Amazon’s public directory of cloud startups .
Inclusion in the AWS Startups Showcase reflects architectural readiness and operational maturity, rather than early-stage experimentation.
To explore an incident-centric security scenario where defensible data trails matter, check out our analysis on stopping construction site diesel theft — Part 2 .
Preparing for SOC 2 readiness
As Trinity Guard® continues to scale across enterprise and multi-site security environments, the platform is actively being prepared for SOC 2 audit readiness.
This preparation includes the structured collection and retention of operational logs, access records, system events, and change histories required to support security, availability, and integrity controls.
Logging and monitoring processes are being aligned to ensure traceability, accountability, and evidence preservation across patrol execution workflows, supervisory actions, and infrastructure-level operations.
This work reflects a broader commitment to operating Trinity Guard® as an enterprise-grade security platform, where infrastructure discipline, data handling, and operational transparency are treated as foundational requirements rather than afterthoughts.
What this means for clients and stakeholders
Clients rarely ask about infrastructure directly. They experience it indirectly.
They notice it when:
- historical data remains consistent,
- audits do not require explanation,
- incident timelines can be reconstructed precisely,
- accountability does not rely on trust alone.
When infrastructure works as intended, it becomes invisible. When it does not, it becomes the point of failure.
As adoption grows and infrastructure demands increase, our focus remains on sustainable scaling, and we do not rule out working with partners who bring deep operational experience from manned guarding, security operations, and large-scale SaaS environments.
The quiet signal behind modern security platforms
The most reliable security platforms do not advertise reliability. They assume it.
They do not overpromise features. They prioritize defensibility, traceability, and operational clarity.
Cloud infrastructure is not the product — but it determines whether the product can be trusted when it matters most.
That distinction separates tools from systems.
See how Trinity Guard® turns patrol activity into audit-ready evidence
If your operation depends on defensible proof — not just reports — your platform has to be built as an evidence system from day one.
FAQ — Cloud infrastructure, AWS, and audit readiness
Why does cloud infrastructure matter for guard tour accountability?
Because accountability depends on data integrity, traceability, and availability. Those guarantees come from infrastructure and logging discipline, not from interface design.
What does being listed in the AWS Startups Showcase signal?
It signals that the product and architecture are presented in an AWS startup community context. For clients, it is an additional trust signal that the platform is built on enterprise-grade cloud infrastructure.
What does “SOC 2 readiness” mean in practice for Trinity Guard®?
It means building and aligning logging, monitoring, access records, system events, and change histories so security, availability, and integrity controls can be evidenced during an audit process.
Does infrastructure reduce disputes with clients?
Yes. When data is consistent, time-synchronized, and audit-ready, service proof does not depend on explanations or manual reconstruction.
